January 13, 2006
FISA and the NSA
The NSA surveillance story has been in the news for a while now, and there has been a great deal of commentary in op-eds and on law blogs about whether the actions taken were legal or not. There are actually two questions about the program's legality: was it unconsitutional (i.e. did it violate the Fourth Amendment) and did it violate statute — specifically the Foreign Intelligence Surveillance Act (FISA). (There are secondary questions about Article II powers and the Authorization to Use Military Force passed after September 11th, but those questions aren't reached unless one of the first two is answered in the affirmative). Now, wanting to understand the issue, I actually read the law and it turns out that a great deal hinges on the definition of "electronic surveillance" in 50 USC 1801(f). Suffice it to say that it's not a simple definition. In fact, it's been likened to Swiss cheese – the idea being that after the Nixon fiasco Congress wanted to be seen as doing something but also wanted to leave enough holes for national security to be protected. Since understanding the definition of "electronic surveillance" is so central to determining whether the NSA program violated FISA, I decided to parse the definition: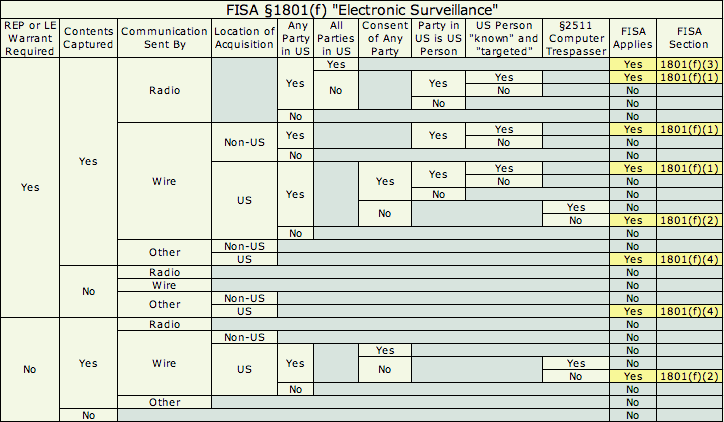 As you can see, there are lots of scenarios (assuming I've read the law correctly) where FISA does not apply. While I'm not sure we currently know enough about the actually workings of the NSA program to know where it falls out in the chart, as more becomes apparent, hopefully this will be useful.
Posted by richard at January 13, 2006 04:05 PM
As you can see, there are lots of scenarios (assuming I've read the law correctly) where FISA does not apply. While I'm not sure we currently know enough about the actually workings of the NSA program to know where it falls out in the chart, as more becomes apparent, hopefully this will be useful.
Posted by richard at January 13, 2006 04:05 PM
I know — I swore not to write again, but here I am. There are other statutes in play, including the Wiretap Act, and the Stored Communications Act. The Wiretap interposes restrictions on the interception of wire, oral, and electronic communications (subject to enumerated exceptions); the SCA doesn't do much at all on this front.
Note 18 U.S.C. § 2511(2)(c), which provides the legal authority for FBI agents to put a wire on Big Pussy and send him off to gather evidence against Tony Soprano.
Another point of interest — an email is not "intercepted" for purposes of the Wiretap Act unless it is received/reviewed while in transmission. Thus it is almost impossible for email surveillance to fall within the scope of the Wiretap Act, because it of necessity is read after it is received by the user. The First Circuit ruled in 2003 on a case in which a company offered email accounts to customers and rigged automatic routing software to forward a copy of certain communications from those accounts to its CEO simultaneously with transmission. The court held that this was an actual email intercept forbidden by the Wiretap Act (and not subject to any exception). A rare case.
The Fifth Circuit held in the 1970s that wire and oral communications had to be intercepted contemporaneously with their transmission, in order to be covered by the Wiretap Act. Congress overrode this requirement with an enactment that broadened the Act's scope to reach recordings. For a period of time "electronic communications" and "wire and oral communications" were treated differently. The USA PATRIOT Act reversed course with wire and oral communications and instituted a contemporaneity requirement to match the one that applied to email — otherwise the Wiretap Act would have made it practically impossible for the government to intercept voice mail.
The Stored Communications Act has no real teeth, but it's what would apply to any email communications that aren't picked up in real time.
I don't find it objectionable that the government is listening in on phone calls between citizens and suspected terrorists (though I'm not sure why obtaining a post hoc warrant from the secret wiretap court wasn't good enough for investigators). My problem is that I can't be sure that they're not doing something more. That is, if we weren't told about the program in the first place, why should we be comfortable with assurances from the government that the program has only a very limited scope?
Anyone could ask the question on any day: how do we know the government isn't doing secret bad things? But I think the question has more bite in this instance, because (1) we know it's doing secret things, but we don't have details, (2) those secret things were amply available under the law, but subject to a negligible check with the wiretap court.
I don't buy the argument that al Qaeda would stop talking if they knew we were listening. al Qaeda has to assume that we're listening, whether or not a particular program is made public. They'd be stupid not to, and we know they're not stupid.
I might buy the argument that the program is exactly what we're being told it is, and that the Administration simply decided it would be easier to get forgiveness than permission on this point.
Maybe I'm not as clear on the facts as I'd like to be. Have I mischaracterized the Administration's alternative course here — to proceed with the taps and get them approved, basically in secret, after the fact by the wiretap court? I don't see what they gained by cutting out the court — unless they were intending to listen in on something that the court couldn't approve.
Posted by: Phutatorius at January 16, 2006 12:31 AMThanks for the pointers. But the Wiretap Act specifically references FISA and seems to except conduct authorized under it. The Stored Communications Act is less straightforward in that, as far as I saw in my quick perusal, it doesn't explicitly except FISA surveillance.
That said, I think both, in their generality, would be a lot less likely to pass muster in restraining the Executive in matters of wartime foreign intelligence than FISA would (assuming FISA would). That is, you'd have a colorable argument that the Youngstown category would change if one was forced to rely on just those two statutes and not FISA.
Now, I agree with some of what you are saying about the wisdom of the program. Qui custodiet ipsos custodes, and all that. But I'm also, I think, more open-minded than you about two things: first, that the current leak may have actually caused harm by alerting the enemy to specific capabilities (if not initially then in the eventual defense of the legality of the program) and second, that ex post (next 72 hour) FISA authorization is a bigger hurdle in time, resources and evidentiary burden than one would originally think (see the pre-9/11 shortcomings of the system).
That being said, I'm certainly not trying with this analysis of the statute to say that the program was legal or a good policy — I just thought it was worth trying to parse out when FISA applied and when it didn't because I kept getting confused myself at all the if, ands, and excepts.
Posted by: richard at January 16, 2006 01:51 AM